It’s been a while since a report on Android malware surfaced, but the assault on the world’s largest mobile platform continues to evolve and develop. It now appears that malware-makers are stepping up their game with Android.Bankosy, a malware strain which can essentially crack the security blanket provided by a voice-based two-factor authentication system.
The latter part of 2015 saw an increase in the number of trojans designed to specifically target sensitive financial data and institutions. That in itself is a big enough worry to trigger some serious concerns not only for financial organizations, but also for anyone who regularly accesses this type of data through an Android-powered device. Security firm Symantec has not only found and investigated a number of those trojans, but has also discovered and identified the aforementioned Android.Bankosy strain, which has added functionality allowing it to deceive two-factor authorization used in banking system voice calls.

Utilizing voice calls as part of a two-factor authorization system is something relatively new to the banking industry. Historically speaking, banks have been utilizing SMS to provide users with a one-time password (OTP) as the secondary stage in a two-factor authentication process. A number of institutions however, have decided to make the move across to providing that time-sensitive password via an automated voice-call as it was deemed to be more secure in theory by those advising the banks on security mechanisms. Clearly this doesn’t appear to be the case as the discovered trojan is capable of intercepting the call and effectively stealing the transmitted data.
It’s actually kind of ironic that the feature was ultimately introduced with the notion of “improving the security” of the process. Symantec’s Dinesh Venkatesan discusses the threat and how it manages to go about its business in stealth:
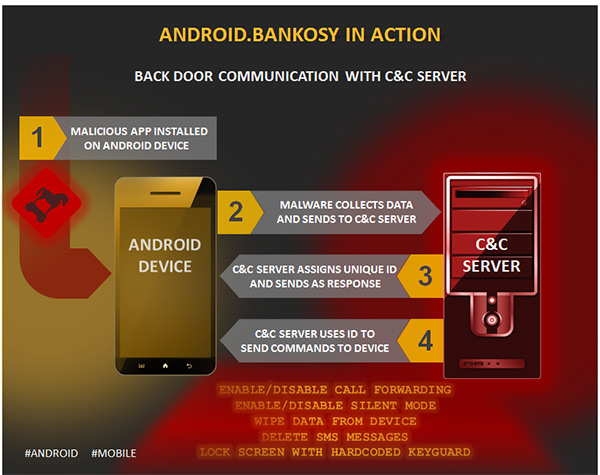
To improve the security of OTP (one time password) delivery, some financial organizations started delivering OTP through voice calls instead of SMS. Once the malware is installed on the victim’s device, it opens a backdoor, collects a list of system-specific information, and sends it to the command and control server to register the device and then get a unique identifier for the infected device. If the registration is successful, it uses the received unique identifier to further communicate with the C&C server and receive commands.
Your best bet to defend yourself against such attacks is to keep your Android OS updated, and to make sure that you install apps from trusted sources only. Also keep an eye out for any permissions an app may ask for when you launch it for the first time.
(Source: Symantec)
You can follow us on Twitter, add us to your circle on Google+ or like our Facebook page to keep yourself updated on all the latest from Microsoft, Google, Apple and the Web.

