Yesterday, MalwareHunterTeam discovered a new variant of the CryptoMix ransomware that is appending the .arena extension to encrypted file names. This family of ransomware releases a new version almost every week, if not sooner, so it will be expected to see another variant released soon with a new extension.
It should also be noted that this ransomware should not be confused with the recent Crysis variant that appends the .arena extension as well. The easiest way to tell the difference between the CryptoMix and Crysis variants, is that the CryptoMix variant will turn the filenames into a hexadecimal strings as described in the next section.
This article will provide a brief summary of what has changed in this new variant. As we are always looking for weaknesses, if you are a victim of this variant and decide to pay the ransom, please send us the decryptor so we can take a look at it. You can also discuss or receive support for Cryptomix ransomware infections in our dedicated Cryptomix Help & Support Topic.
Changes in the ARENA Cryptomix Ransomware Variant
While overall the encryption methods stay the same in this variant, there have been some differences. While the ransom note filename continues to be _HELP_INSTRUCTION.TXT, it now uses the ms.heisenberg@aol.com email for payment information.
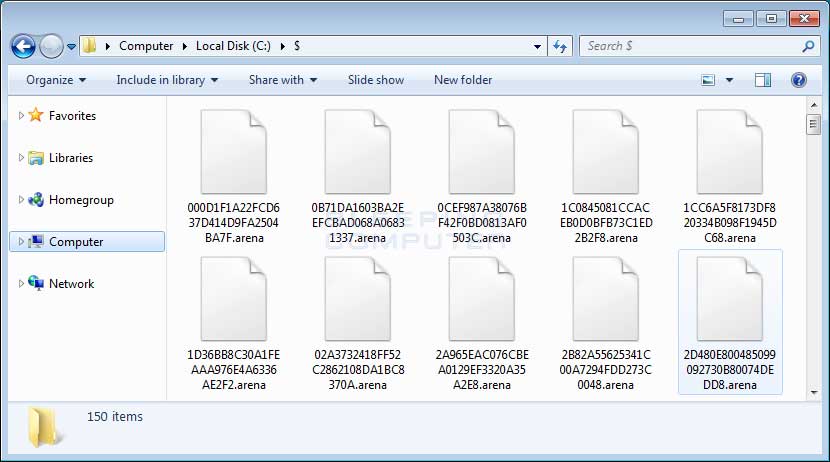
The next noticeable change is the extension appended to encrypted files. With this version, when a file is encrypted by the ransomware, it will modify the filename and then append the .arena extension to encrypted file's name. For example, a test file encrypted by this variant has an encrypted file name of 0D0A516824060636C21EC8BC280FEA12.arena.
This variant also contains 11 public RSA-1024 encryption keys that will be used to to encrypt the AES key used to encrypt a victim's files. This allows the ransomware to work completely offline with no network communication. This variants 11 public RSA keys are different from the ones used by the previous Empty Cryptomix Ransomware variant.
As this is just a cursory analysis of this new variant, if anything else is discovered, we will be sure to update this article.
How to protect yourself from the Arena CryptoMix Ransomware
In order to protect yourself from the Arena variant of CryptoMix , or from any ransomware, it is important that you use good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
You should also have security software that contains behavioral detections such as Emsisoft Anti-Malware or Malwarebytes. Regardless of the security software you use, make sure it contains behavioral detections so you do not have to rely on signatures or heuristics.
Last, but not least, make sure you practice the following good online security habits, which in many cases are the most important steps of all:
- Backup, Backup, Backup!
- Do not open attachments if you do not know who sent them.
- Do not open attachments until you confirm that the person actually sent you them,
- Scan attachments with tools like VirusTotal.
- Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
- Make sure you use have some sort of security software installed.
- Use hard passwords and never reuse the same password at multiple sites.
For a complete guide on ransomware protection, you visit our How to Protect and Harden a Computer against Ransomware article.
IOCs
File Hashes:
SHA256: 3d615c210addb2672e40b291c2bf7f322955e7df475512a60d682ef1110ff511
Filenames associated with the ARENA Cryptomix Variant:
_HELP_INSTRUCTION.TXT
C:\ProgramData\[random].exe
Registry entries associated with the ARENA CryptoMix Variant:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[random]"="C:\ProgramData\[Random].exe""
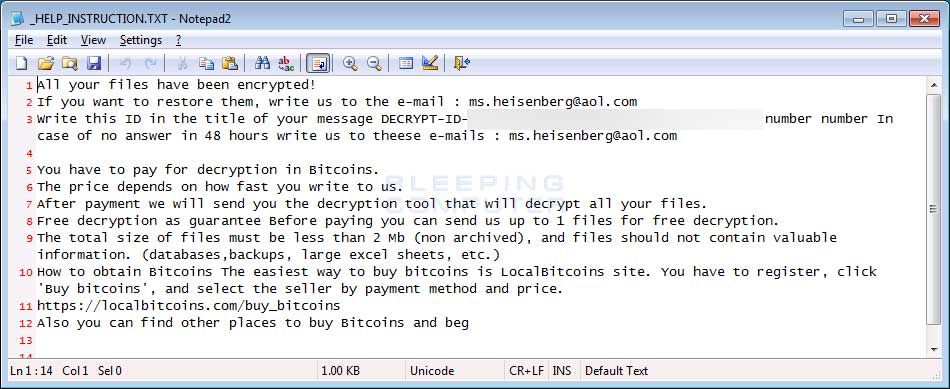
ARENA Ransom Note Text:
All your files have been encrypted!
If you want to restore them, write us to the e-mail : ms.heisenberg@aol.com
Write this ID in the title of your message DECRYPT-ID-[id] number number In case of no answer in 48 hours write us to theese e-mails : ms.heisenberg@aol.com
You have to pay for decryption in Bitcoins.
The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee Before paying you can send us up to 1 files for free decryption.
The total size of files must be less than 2 Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price.
https://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beg
Emails Associated with the ARENA Ransomware:
ms.heisenberg@aol.com
Executed Commands:
sc stop wscsvc
sc stop WinDefend
sc stop wuauserv
sc stop BITS
sc stop ERSvc
sc stop WerSvc
cmd.exe /C bcdedit /set {default} recoveryenabled No
cmd.exe /C bcdedit /set {default} bootstatuspolicy ignoreallfailures
C:\Windows\System32\cmd.exe" /C vssadmin.exe Delete Shadows /All /Quiet
Bundled Public RSA-1024 Keys:
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDA3BRgzCL3mmmPIKa8ZLsOWcbodwdpNArYdLO5PQ5enUQYr572jmnGoF5WKy65p41H7WTeWV/ZMXHKUJS87daeGI/C YvPlgpx6ZDuqSVxMLgXDM1vKbJeuoWuZSeo+Kdy1W22CD3amy3a1HCISX068zaVr wKkQqaz3tS2h+JYZ/wIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCAcL2bv8UxRqZ6DD5VHvsNCAh/ e18CEHVeff1kfCDIB4D9q3/Yu59Mq9P5H7E94m0YlN57eZmJ7uiJth/6/MExv+uw L5izNB/b5CKMuSaqqUsQY27P3yTIfSyWrqQ6Hk2TDljytlvceSFwpWdEFn6B5a5p KnRMzKMSre7zrIUm+QIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCK3KhGZ0Tp5NnWzTT8qQSoXNBf noIUpn3M1ubJf8Z6lb2xGWIYPDpmF+H4yKTPZ20vc49SQ6Dbrdwc0/6TzykOMdOv 9BJWYT75kwEufiqv0Gy9ZHKhlpAXJkrWoOMonFqS4T6HOTdkiN+shadQt299bUlu f+TqSqhkhz6Cp9IHbwIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC8tcLsf2h4fuaJRl9CBkDA5Bs+ CnqGgyOyi3ntolggyIyFcUtiU2mCHMBANUnAjp5Hxk0ODI4ZtlokYgpOWZOP6XYV r5ZGTRzz1IN7ahOSFTpMwCqlafPPqzdAWINdFWQUAaNtNxYwo6jCRyeTTKKNWpH3 Ia4iP9SJjXaytOtbzQIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCC6OGfuH1Ht732u4UomMTGb1Kd uQawHQUvhMYzFrWK3x5IMCXnkjJCfGEBcF0FqIMTiYQsY4v2I/71nntIUFLn/usO McdJMMoXCZcErvV8PFRYz7p3QEqKnleUJt10ncib7pZkgqfP5cSx7xymJnj+/fZH 9yVmOlshSkZqNbt6dwIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCk9ZSRC7RxXXihK28uJzFY5iAY 2mgaUU16jGijYai5rZGCt5e9+e412HuPlQYvueOsK7bkyCKlnITbYCzYDOXv+k++ Kk9qi7atez0EcPT77cSrWoC/ENFsmdX/kznw3nbxjyVkoSZzFh+MPM50xCl1f05b eHUwrrAaI82GTtQ7DQIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCHAlC0tOBzqZxJbBpF9qi7jVIz GKmop5KMyZ0SmtShlC4ily37+/TllLq0GWfcUlmepUogmuebAHYFFxblH9PaNCwv MNo+HjMJBLHBchvH4buKtmf/ctaGf3CxFmegE9vG/ne9JiSx6IGe5sK1KZbCPqSO X3IpyKirdSCn33QqWwIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCRyCG1kAYipMRe9NKbYX7Z6ndN Ngt3s0sQ1eAYE9+Swnl7etg3KaOhbW0RXIXWW6jMxwrBrGC9JXoLeSe3jREf1lWI nPw/p2GKvERVuf1V+LG0n7fPlKPDLWGhUwi4LxiHmZhrygkG+PBQEhPhyiM7db84 F+QbhSzrRpgPKnMeTQIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC9n6bm9GC3UQ8OOB+ahHYuIS3k jkUBOXyKEJKaiebSShdi5pUDAxiObWcks9Ql9Vb/z0S+6h0Ot1iOH9jUQlWlQ8Kt SOoli2eg/Jq42PWL4qW7ejc6qO8KmPvMtsZEqrcwC9Xv0lpx50Xp+cXXf+DUIhhS 7DOwxl7QGcts+oGkpwIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC61mhlwTQ1ZfkjWzTVD5LIvRB+ K87a51nEGOeXBHg8zTGYuZfd0vVh+p9G2p1wNtV9pzfHmzVOBGVVl0pGfB+J4DBP XYUWXYOTswCKRr0jI/xc9Xj9OFqfTJ57mRRb7tcsQyqtwdD90G+9cnftgJsh7XKW cBrGYGrFO7FofO0c/wIDAQAB
-----END PUBLIC KEY-----
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCJdY+JyIV0ZS0QtaD4qvBUl9zI 1Sgt0D1AABnFLoPWJeZsuFnlTf20AS8nfsf0KTPnLFPRx6VKE4DcW66d+Y6gjvnn HfaKU9m+N4KWFV3kyuI3QIaNRDTbcwebA6/93lS9mpNBrOJOhkesYmOJgH80tzOP iYvj9fsEUzVtHNewMwIDAQAB
-----END PUBLIC KEY-----


Comments
MarkInBucks - 6 years ago
These guys are not playing their game equitably.
They have left many hanging after taking delivery of ransom.
And if you don't respond or delay, they double the ransom to $12,000 USD.
There is no negotiating, no return on payment and I suggest everyone refuse payment.
Until we cut off their revenue stream, they'll keep going.
I remember when this crap started with initial $300 ransoms and now we're up to multiple thousands on first pass.
Sickning
backfolder - 6 years ago
I totally agree Mark. Sadly the way is getting internet and windows OS, could be the end. I have never see much ransom as nowadays.
track3r - 6 years ago
Hey Mark, did you ever get the decrypt tool after paying? I have a customer who is considering paying.
tom21186236001 - 6 years ago
you don't get the key. they just ask for more money.
lolz84 - 6 years ago
Has anyone found a way to decrypt? This is heartbreaking. all my kids photos are on multiple backup drives. they all got encrypted.
tom21186236001 - 6 years ago
they do not release the key after paying. first they ask for more money, when you pay that they never reply to you!