A new strain of ransomware, called Bad Rabbit, began hitting organizations throughout Russia and Eastern Europe on Wednesday (Oct. 25). The malware is being spread through compromised websites, presenting itself as an Adobe Flash Player download.
“When users visited one of the compromised websites, they were redirected to 1dnscontrol[.]com, the site which was hosting the malicious file,” according to a blog post by Talos, Cisco’s threat intelligence team.
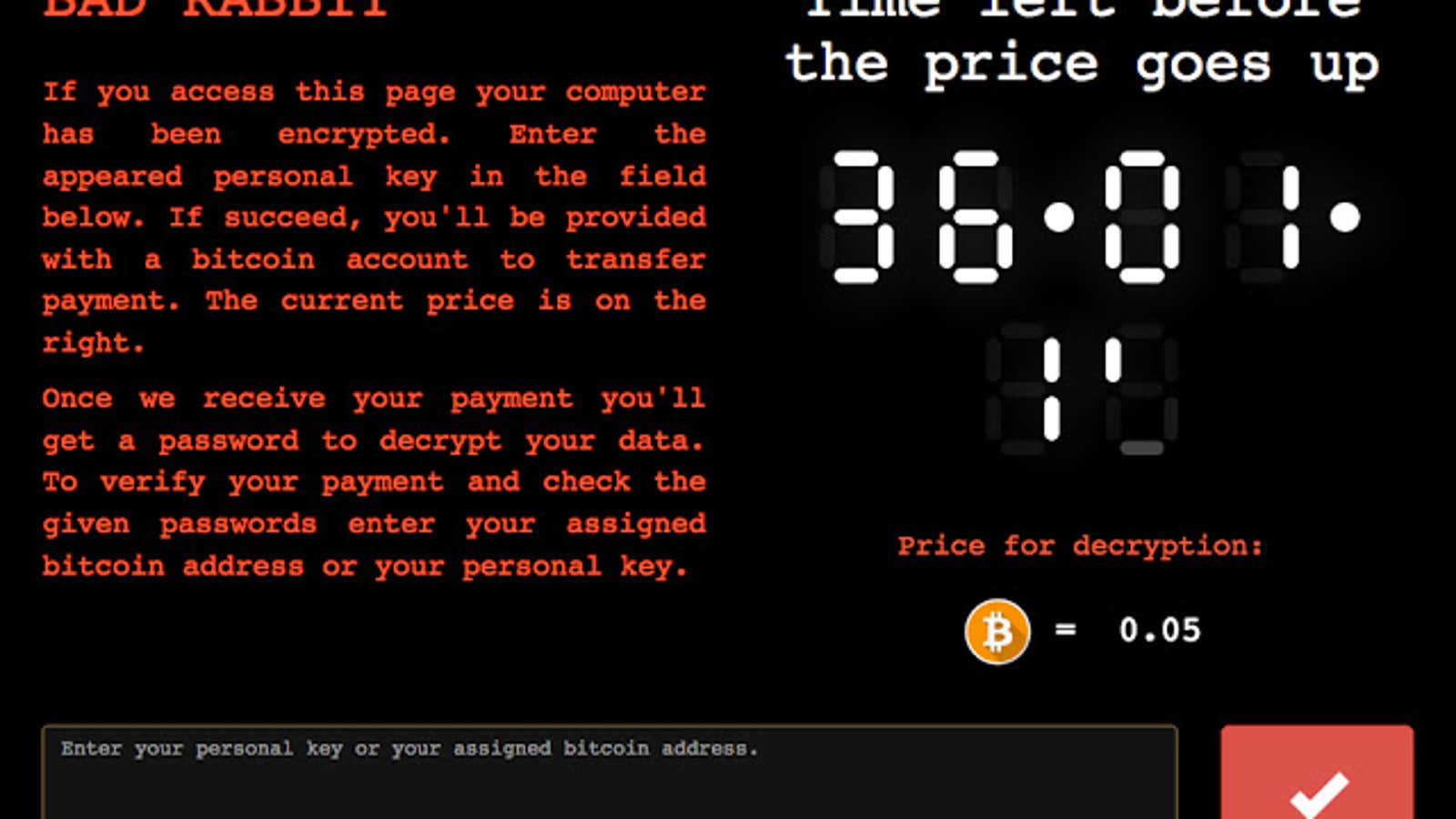
Once infected with the ransomware, victims are directed to a web page on the dark web, which demands they pay 0.05 bitcoin (roughly $285 USD) to get their files back.
After one computer on a network is infected, Bad Rabbit can quickly and covertly spread through an organization without being detected. Although the ransomware has been detected in several countries, it appears to be concentrated in organizations in Russia and Ukraine, particularly media outlets.