Over the weekend, the GandCrab V4 Ransomware was released with numerous changes. These changes include a different encryption algorithms, a new .KRAB extension, a new ransom note name, and a new TOR payment site.
Unfortunately, at this time, victims of GandCrab v4 cannot decrypt their files for free. As always if you wish to discuss this ransomware or receive help with it, you can use our GandCrab Help & Support topic.
GandCrab v4 distributed via fake crack sites
According to a malware analyst who goes by the alias Fly, one of the methdos GandCrab v4 is being distributed is through fake software crack sites. The ransomware distributors will hack legitimate sites and setup fake blogs that offer software crack downloads. When a user downloads and runs these cracks, they will install the GandCrab Ransomware onto the computer.
You can see an example of one of these fake crack blogs below.
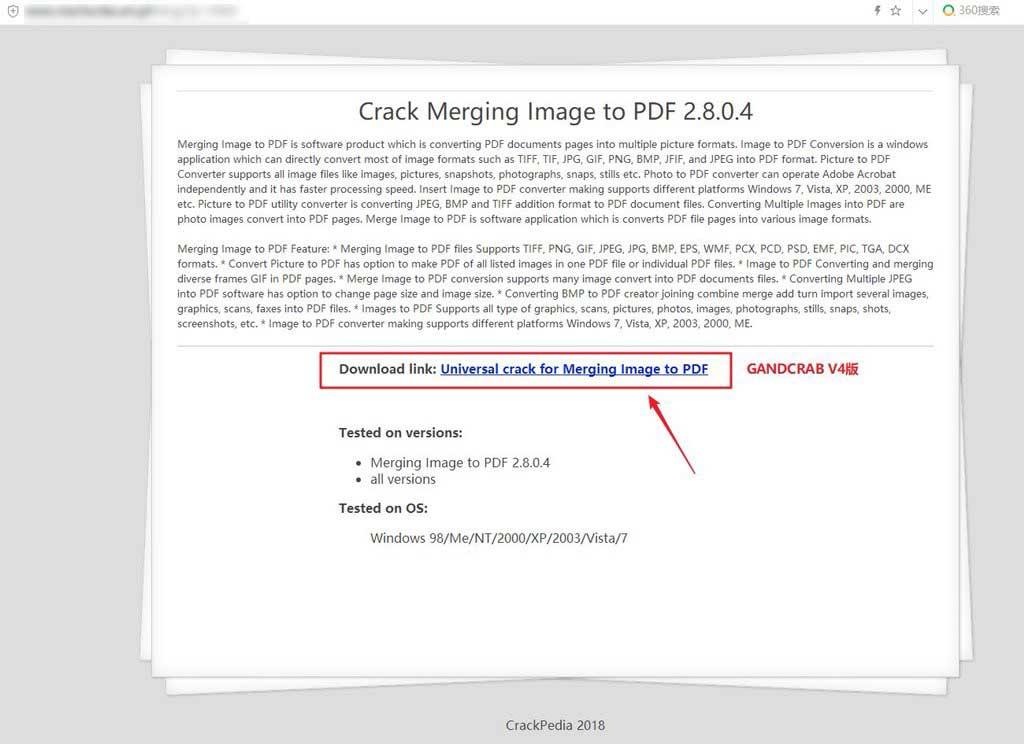
GandCrab begins using the Salsa20 encryption algorithm
According to debug messages found in GandCrab v4 by Malwarebytes security researcher Marcelo Rivero, it appears that the ransomware has switched its encryption algorithm to Salsa20.
#GandCrab V4 internal version: 4.0 - seems to use now #Salsa20 stream cipher pic.twitter.com/Op01bBC50g
— Marcelo Rivero (@MarceloRivero) July 3, 2018
The GandCrab authors love to send shout outs to various researchers, companies, and sites and with this change in their algorithm, they sent a message to Daniel J. Bernstein, a computer science professor at the University of Illinois at Chicago who invented the Salsa20 algorithm.
@hashbreaker Daniel J. Bernstein let's dance salsa <3
How GandCrab encrypts a computer
When GandCrab is executed it will scan the computer and any network shares for files to encrypt. When scanning for network shares, it will enumerate all shares on the network and not just mapped drives.
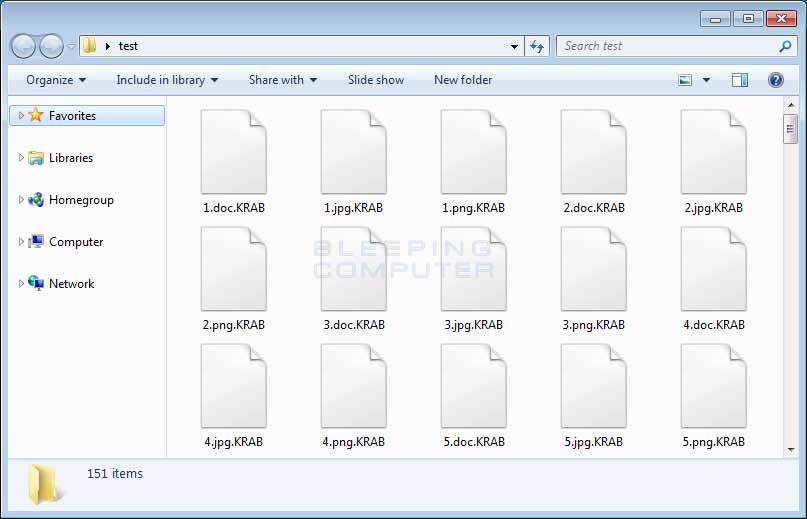
When it encounters a targeted file, it will encrypt the file and then append the .KRAB extension to the encrypted file's name. For example, test.doc would be encrypted and renamed to test.doc.KRAB.
You can see an example of a folder with encrypted .KRAB files below.
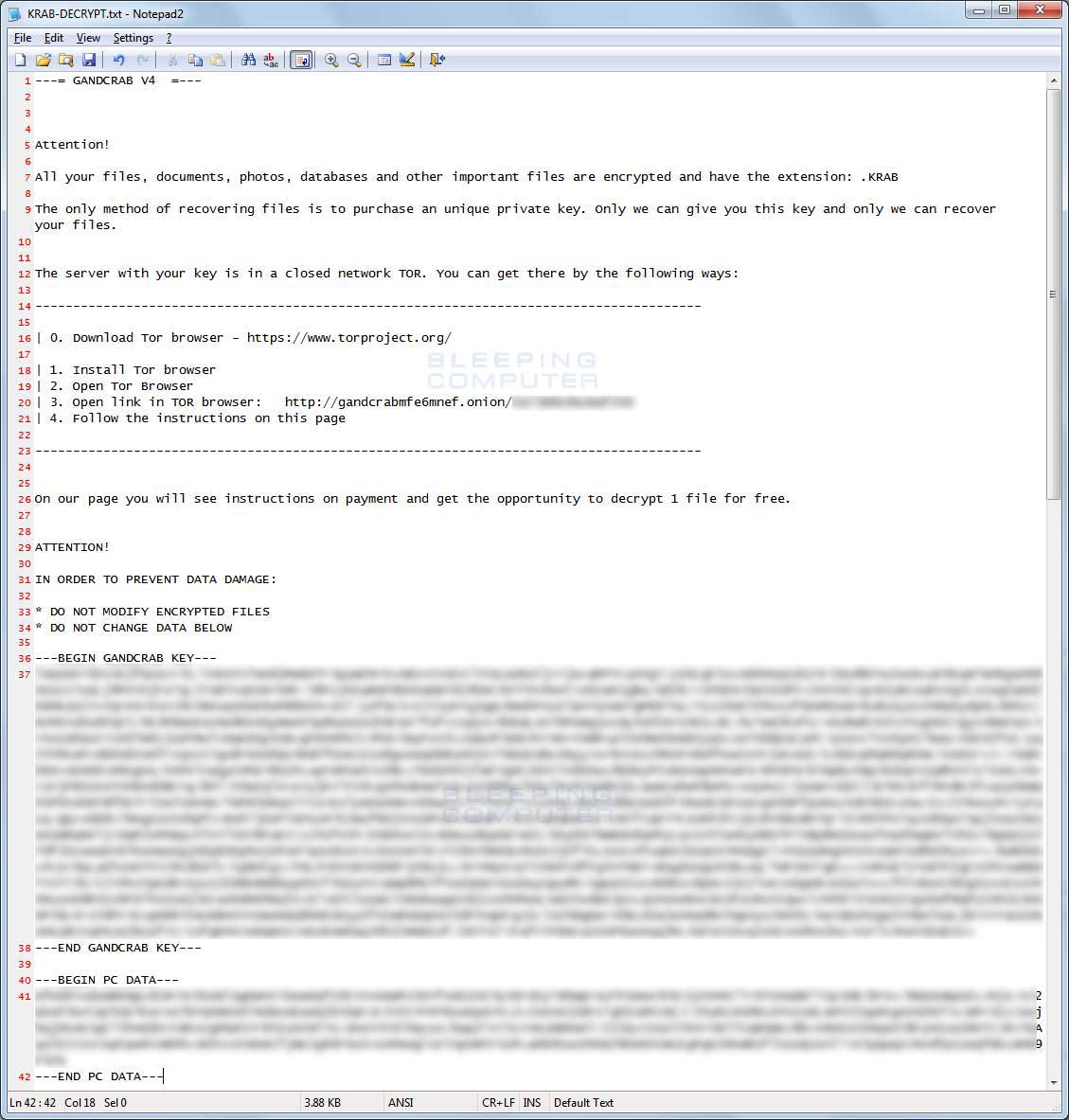
When encrypting files, the ransomware will also create ransom notes named KRAB-DECRYPT.txt that contains information about what happened to the victim's files, a TOR site (gandcrabmfe6mnef.onion) to connect to for payment instructions, and encrypted information that the ransomware developers need to recover your encryption key.
You can see an example ransom note below.
If a user visits the TOR payment site they will be presented with the ransom amount and instructions on how to pay it in order to receive the GandCrab Decryptor.
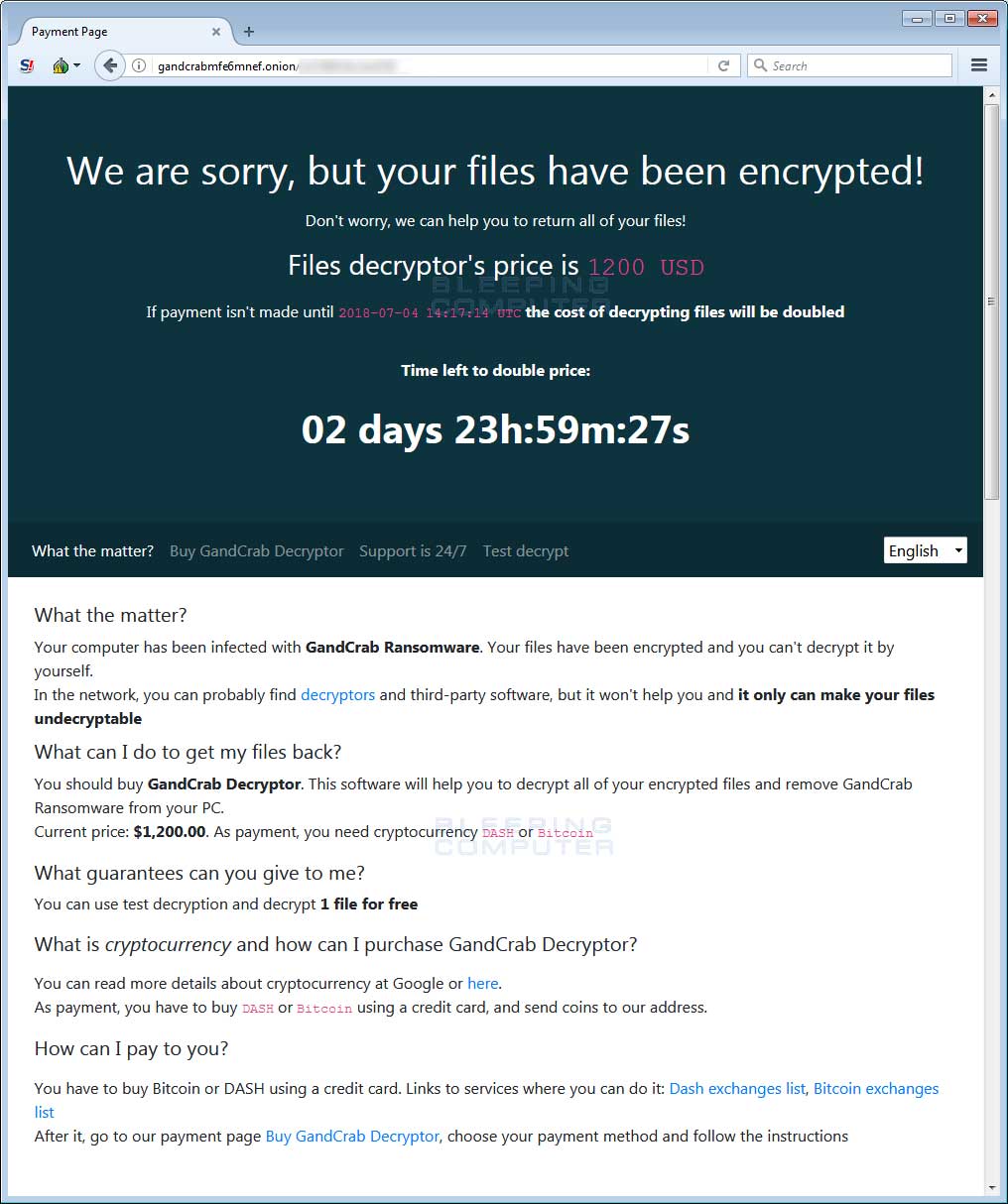
The ransom amount is currently $1,200 USD to be paid in the DASH (DSH) cryptocurrency as can be seen below.
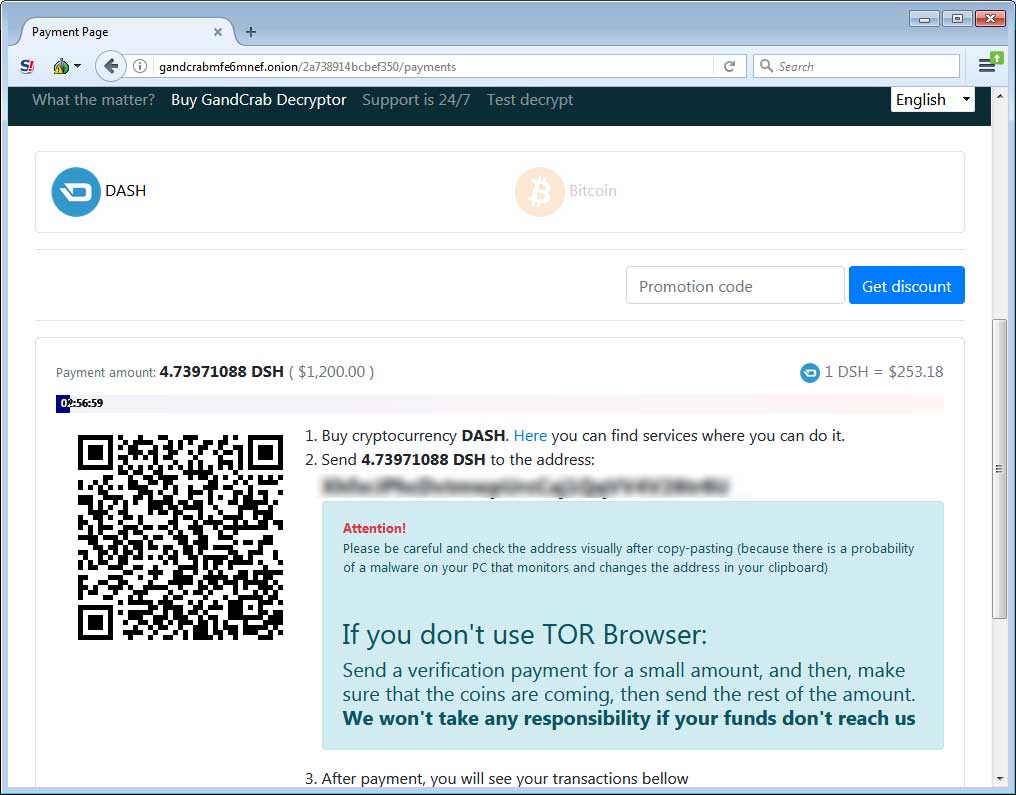
The TOR payment site also includes a support section where you can send messages to the developers and the ability to decrypt one file for free, so that they can prove they can do so.
It goes without saying that victims should make every effort not to pay the ransom. If you have a backup, even if its missing a few files, it is suggested that you still not pay the ransom.
As previously stated, at this time, victims of GandCrab v4 cannot decrypt their files for free. As always if you wish to discuss this ransomware or receive help with it, you can use our GandCrab Help & Support topic
How to protect yourself from the GandCrab Ransomware
In order to protect yourself from ransomware it is important that you use good computing habits and security software. The most important step is to always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
You should also make sure that you do not have any computers running remote desktop services connected directly to the Internet. Instead place computers running remote desktop behind VPNs so that they are only accessible to those who have VPN accounts on your network.
A good security software solution that incorporates behavioral detections to combat ransomware and not just use signature detections or heuristics is important as well. For example, Emsisoft Anti-Malware and Malwarebytes Anti-Malware both contain behavioral detection that can prevent many, if not most, ransomware infections from encrypting a computer.
Last, but not least, make sure you practice the following security habits, which in many cases are the most important steps of all:
- Backup, Backup, Backup!
- Do not open attachments if you do not know who sent them.
- Do not open attachments until you confirm that the person actually sent you them,
- Scan attachments with tools like VirusTotal.
- Do not connect Remote Desktop Services directly to the Internet. Instead, make sure they can only be accessed by logging into a VPN first.
- Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
- Make sure you use have some sort of security software installed that uses behavioral detections or white list technology. White listing can be a pain to train, but if your willing to stock with it, could have the biggest payoffs.
- Use hard passwords and never reuse the same password at multiple sites.
- BACKUP!
For a complete guide on ransomware protection, you visit our How to Protect and Harden a Computer against Ransomware article.
IOCs
Hashes:
ef7b107c93e6d605a618fee82d5aeb2b32e3265999f332f624920911aabe1f23
Associated Files:
KRAB-DECRYPT.txt


Comments
Pointless_noise - 5 years ago
Is this version of GandCrab still calling back to a .bit domain C&C server before execution?
Lawrence Abrams - 5 years ago
No, its quiet now. Does not call back.
Mr.Tom - 5 years ago
It's been about two years since I've run into any computers in the shop that got hit by ransomware. I thought this was getting more popular. These programmers need to step up their game.
Samidar - 5 years ago
Ok so two part question. My secondary pc was infected by this ransomware. Can it infected other PC's connected to the network? My primary pc shows a "program" enabled in thetask managers startup tab with no access to location or info. Also if a ransomware program were already known on a networked pc would a system restore on another pc get rid of or prevent the virus from executing?
DataMedic - 5 years ago
When is Microsoft going to get wise to this and come out with a new file system which actually has versioning of files and/or the ability to detect a program encrypting mass amounts of files?