Since September 2016, a criminal group has been using different versions of the Crysis ransomware to infect enterprise networks where they previously gained access to by brute-forcing workstations with open RDP ports.
According to Trend Micro, the security firm who first discovered the attacks and has been keeping an eye on the group's activities, incidents more than doubled in January 2017, compared to previous months.
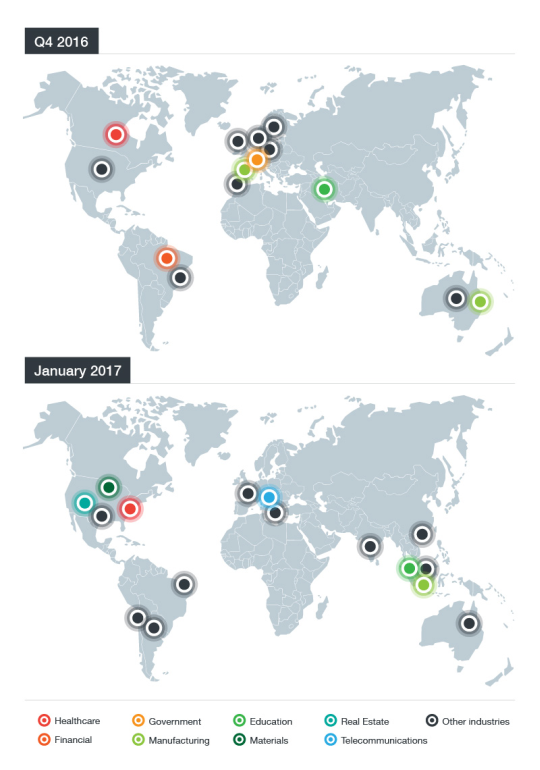
While initial attacks only targeted small companies in Australia and New Zealand, according to Trend Micro, the group has slowly expanded to new territories and has also started to target larger enterprises as well.
According to statistical data from last month, the group has been very active in targeting healthcare organizations in the US.
The problem: User accounts with weak credentials, open RDP ports
A typical infection goes through the following steps. An attacker picks targets with RDP ports available online and identifies if the computer is assigned to an enterprise network. Alternatively, he can always buy access to previously hacked RDP servers, via marketplaces like xDedic.
Once he purchased or gained access to a computer by brute-forcing the RDP connection with basic username-password combos, the attacker downloads and then manually executes a version of the Crysis ransomware on each of the hacked computer.
If the attacker manages to gain access to multiple workstations inside the same company, Trend Micro says attackers won't shy away from infecting all targets, sometimes with different versions of the Crysis ransomware, each with different features. In one specific case, Trend Micro reported seeing the group install six different Crysis versions in the span of only ten minutes.
RDP connections are a common channel for spreading ransomware
The attack scenario is not "innovative" in any way since there have been multiple ransomware strains and groups that relied on brute-forcing RDP ports to infect their victims.
The list includes names such as LowLevel, DMA Locker, Apocalypse, Smrss32, Bucbi, Aura/BandarChor, ACCDFISA, or Globe.
In November 2016, an unknown user posted a trove of master decryption keys for the Crysis ransomware on the Bleeping Computer forums. Most of these keys are now outdated.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now