Lots of small little updates with no big news from any major Ransomware distributions.
Of particular note is the fact that the Samas gang has made $450,000 from their operation, which may not be that big compared to some of the others, but has a much lower distribution as well. Another item to watch out for the holidays when people are buying presents is that Cerber is now sending spam pretending to be credit card purchase notifications.
Last, but not least, Emsisoft, Bitdefender, Check Point, and Trend Micro have been added as associated partners to the No More Ransom organization.
Contributors and those who provided new ransomware information and stories this week include: @BleepinComputer, @fwosar, @demonslay335, @struppigel, @malwrhunterteam, @campuscodi, @PolarToffee, @DanielGallagher, @kafeine, @JAMESWT_MHT, @jiriatvirlab, @Seifreed, @nyxbone, @drProct0r, @proofpoint, and @msftmmpc.
If you are interested in ransomware or InfoSec, I suggest you follow all of them on Twitter.
Update 12/18/16: Removed LevisLocker, which is a "Joke Ransomware" used to mess with Tech Support Scammers.
December 10th 2016
CHIP Ransomware uses the Dale Extension for Encrypted Files.
In homage to the Chip & Dale Disney characters, Michael Gillespie discovered that the CHIP ransomware now uses the Dale extension for encrypted files. This ransomware uses grion@protonmail.com, grions@protonmail.com, grion@techie.com, grion@dr.com as email addresses to contact for payment instructions.

In-Dev Deadly_60 Screen Locker Discovered
I discovered a new screen locker with an incredibly annoying matrixesque background animation. Does not encrypt any files.

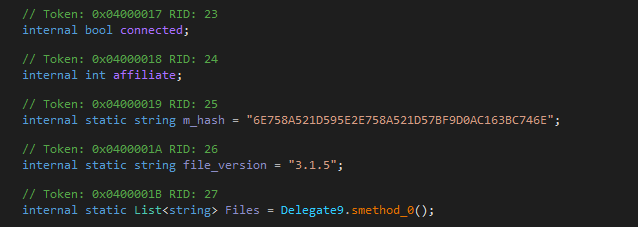
PadCrypt Ransomware 3.1.5 released
I found a sample of the PadCrypt Ransomware showing that it's version is now 3.1.5. Not much more to say on this one.
M4N1F3STO Virus Screen Locker Discovered
Jiri Kropac discovered a screen locker called M4N1F3STO Virus. The unlock code can be found here.

December 12th 2016
Samas Ransomware Group Made at Least $450,000
Microsoft Malware Protection Center released a report about how the criminal group being Samas has made at least $450,000 by infecting organizations with the Samas ransomware in the past year, according to an analysis by researchers from security firm Palo Alto Networks.
PayDay Ransomware based on Hidden-Tear Discovered
I discovered the PayDay Ransomware, which is based off of Hidden-Tear. PayDay uses a background from the PayDay video game and is written in Portuguese. When it encrypts files it will append .sexy to encrypted files and creates ransom notes called !!!!!ATENÇÃO!!!!!.html.

You Have Been Hacked!!! Ransomware
MalwareHunterTeam discovered a new in-dev ransomware titled You Have Been Hacked!!!. When it encrypts a file it will append the .Locked extension to the file. This ransomware will also attempt to steal passwords, which it will display when you click on the Full list of passwords button. Whether or not it actually will leak them is unknown.

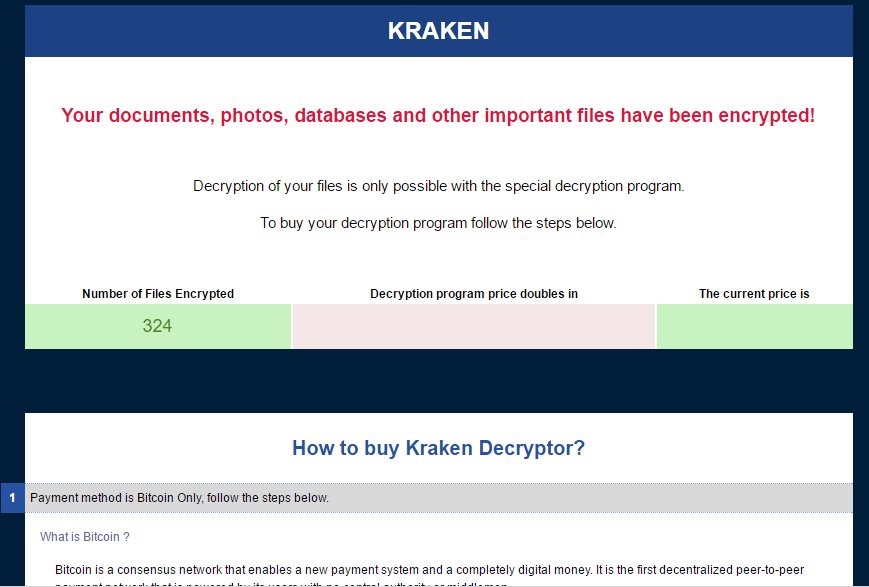
Kraken Ransomware Discovered
Michael Gillespie discovered a new ransomware called Kraken. This ransomware will rename encrypted files to [base64].kraken and create ransom notes called _HELP_YOUR_FILES.html.
December 13th 2016
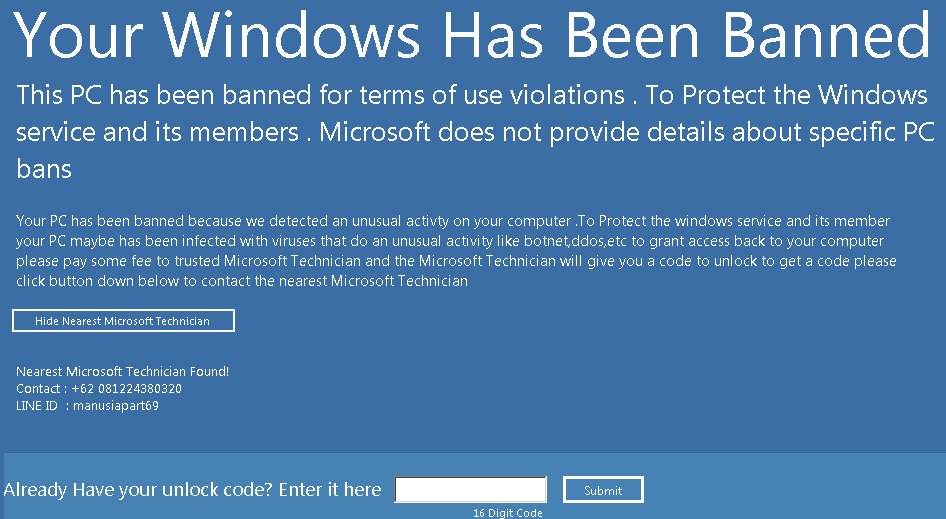
New Screen locker called Windows Has Been Banned
Jiri Kropac discovered a new variant of a previously released screenlocker that is now titled Windows Has Been Banned. The unlock code is nvidiagpuareshit.
CryptoMix updated to use New Extension
Malware researcher xXToffeeXx discovered a new variant of the CryptoMix ransomware that is using the .email[supl0@post.com]id[\[[a-z0-9]{16}\]].lesli extension for encrypted files and creates ransom notes titled INSTRUCTION RESTORE FILE.TXT.
Locked-In Decryptor Released
Michael Gillespie released a decrypted for the Locked-In Ransomware. Information on downloading and using the decryptor can be found here.
December 14th 2016
Cerber Ransomware Spreads via Fake Credit Card Email Reports
Just in time for the Christmas holiday shopping spree, Microsoft Malware Protection Center has discovered that the group behind the Cerber ransomware has launched a spam campaign that uses fake credit card reports to trick users into opening a Word file that under certain circumstances will download and install the deadly Cerber ransomware.
New Xorist Ransomware that uses the .antihacker2017 Extension
I found a new Xorist variant that appends .antihacker2017 to encrypted files. Emsisoft's decryptor will handle it.

New Globe variant that uses the unlockvt@india.com Extension
R0bert R0senb0rg discovered a new Globe variant that uses the unlockvt@india.com extension for encrypted files.

CIA Special Agent 767 Screen Locker Discovered
I discovered a new variant of the M4N1F3STO Virus, but now uses a different background. The unlock code can be found here.

New variant of the FenixLocker Discovered
GData malware analyst Karsten Hahn has discovered a new variant of the FenixLocker Ransomware. This variant uses the ransom note Help to decrypt.txt and the email address thedon78@mail.com for payment instructions.
New In-Dev Koolova Ransomware only Encrypts the Test Folder
xXToffeeXx discovered the in-dev Koolova ransomware with Italian text that only targets the Test folder on the user's desktop.

December 15th 2016
No More Ransom Project Expands with 34 New Partners, 32 New Free Decryption Tools
Bitdefender, Check Point, Emsisoft and Trend Micro are now associated partners with NoMoreRansom, a title reserved for companies that directly contribute to the development of new unique decryption tools and decryption keys.
New BandarChor Ransomware Variant Spreads via Malvertising on Adult Sites
ProofPoint security researcher Kafeine has discovered that malicious ads displayed on several adult websites and a store selling quadrocopters (drones) are infecting visitors with a new version of the BandarChor ransomware.
Someone named Chris is playing with Hidden-Tear
Chris is playing with the Hidden-Tear Ransomware. Someone should tell his parents.

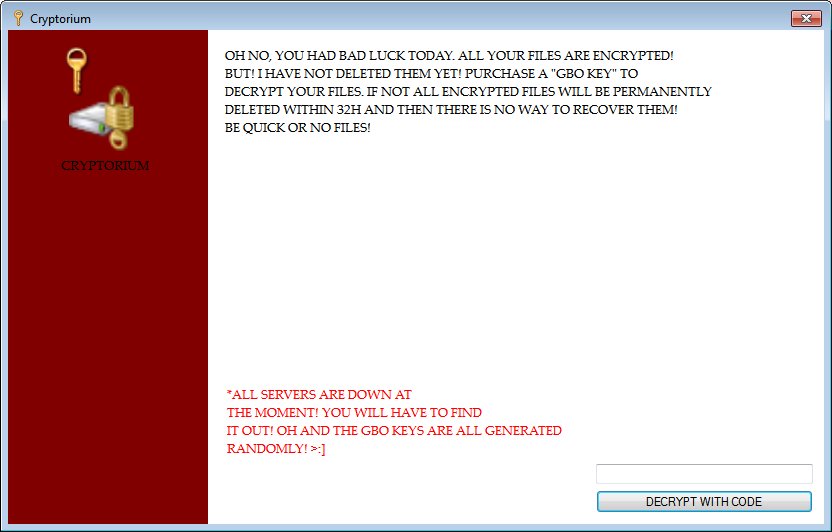
New Cryptorium Ransomware Discovered
Karsten Hahn has discovered a new ransomware called Cryptorium. Cryptorium only renames files and does not encrypt them. Appends the .ENC extension to renamed files.
December 16th 2016
Unknown Ransomware discovered that impersonates Globe
MalwareHunterTeam discovered an "Unknown ransomware" sample that impersonates Globe. Uses the ransom note HOW_OPEN_FILES.hta and appends the .crypt extension to encrypted files. Uses the email address alex_pup@list.ru for payment contact.

Cerber Ransomware using a new IP range for UDP Statistics
MalwareHunterTeam discovered that Cerber has changed the IP ranges used for UDP stats. It now uses the 37.15.20.0/27, 77.1.12.0/27, and 91.239.24.0/23 IP ranges..
New variant of the Globe Rnasomware discovered using the Email Address rescuers@india.com
xXToffeeXx discovered another variant of Globe with a different note format and using the extension .rescuers@india.com.3392cYAn548QZeUf.lock.



Comments
Fluttershy - 7 years ago
Lol, Levis Locker wasn't discovered by that guy FYI. It's mine. :)
Lawrence Abrams - 7 years ago
Removed info about it.