This week we have seen a lot of CryptConsole variants, Magniber activity, and smaller variants released. Ransomware continues to decline as malware developers move toward more profitable miners and information stealing Trojans. Ransomware is not going away, but is instead moving away from mass malspam campaigns to targeted network attacks where a ransom payment may be more likely.
Contributors and those who provided new ransomware information and stories this week include: @demonslay335, @campuscodi, @malwareforme, @DanielGallagher, @struppigel, @malwrhunterteam, @Seifreed, @FourOctets, @fwosar, @hexwaxwing, @BleepinComputer, @jorntvdw, @PolarToffee, @LawrenceAbrams, @Damian1338B, @GrujaRS, @JakubKroustek , @bartblaze, and @leotpsc.
June 2nd 2018
CryBrazil Ransomware Discovered
MalwareHunterTeam discovered a ransomware called CryBrazil that appends the .crybrazil extension to encrypted files. Uses a nicely designed ransom note.

June 4th 2018
New Magniber campaign was underway
Michael Gillespie spotted a new Magniber Ransomware campaign targeting South Korea.
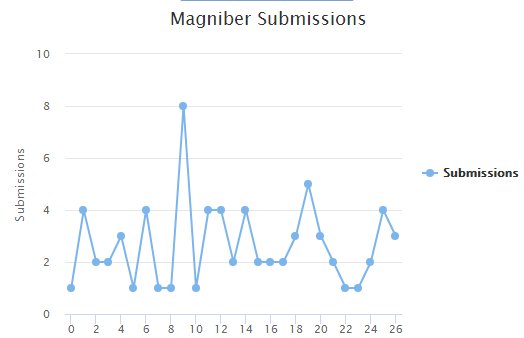
New destructive Pedcont Ransomware discovered
Leo found a new destrucrtive ransomware called Pedcont that claims to encrypt files because the victim has accessed illegal content on the deep web. The screen then goes blank and becomes unresponsive.
New Scarab variant called DiskDoctor
Amigo-A found a new Scarab Ransomware variant called DiskDoctor that appends the .DiskDoctor extension and drops a ransom note named HOW TO RECOVER ENCRYPTED FILES.TXT.

June 5th 2018
New XiaoBa variant uses a Hitler background
MalwareHunterTeam found a new XiaoBa Ransomware variant that uses the .AdolfHitler extension and drops a ransom note named # # DECRYPT MY FILE # #.bmp .

New CryptConsole variant
Michael Gillespie spotted another variant of the CryptConsole Ransomware that uses the xser@tutanota.com email address. Victims can contact him for decryption.
June 6th 2018
Years of Police Dashcam Video Lost in Atlanta Ransomware Incident
The Atlanta Police Department has lost years worth of police car dashcam videos following the March ransomware attack that affected most of the city's IT infrastructure.
RedEye Ransomware Discovered
Jakub Kroustek discovered the RedEye Ransomware, which appends the .RedEye extension and wipes the contents of the files. RedEye can also rewrite the MBR with a screen that gives authors contact info and YouTube channel. Bart also wrote an article on this ransomware detailing how it works and what it does on a system.
The ransomware author contacted BleepingComputer and told us that this ransomware was never intended for distribution and was created just for fun.

New Aurora Ransomware variant
Michael Gillespie spotted a new Aurora variant uploaded to ID Ransomware that uses the #RECOVERY-PC#.txt ransom note.
New CryptConsole variant
ID Ransomware spotted another CryptConsole variant that uses the redbul@tutanota.com email address. Victims can contact Michael Gillespie for decryption.
June 7th 2018
New CryptConsole variant
Michael Gillespie found a new variant of the CryptConsole ransomware that uses the address heineken@tuta.io and is still decryptable.
New GlobeImposter variant
GrujaRS discovered a new variant of the GlobeImposter Ransomware that uses the extension .emilysupp.

June 8th 2018
Princess Ransomware being sold on underground sites
Damian1338 discovered the Princess Ransomware being sold on an underground criminal site.

New PGPSnippet Variant
MalwareHunterTeam discovered a new variant of the PGPSnippet Ransomware that appends the extension .digiworldhack@tutanota.com to encrypted files. Victims can contact Michael Gillespie for decryption.

Test Spartacus Ransomware variant
Michael Gillespie found a test version of the Spartacus Ransomware that uses the emails example@gmail.com and example1@gmail.com and appends the .SF extension to encrypted files.
New Magniber Ransomware variant
A new variant of the Magniber Ransomware was uploaded to ID Ransomware that uses the .ndpyhss extension for encrypted files.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now